Cybersecurity Awareness: Phishing
What is phishing?
A spoof on the sport of fishing, phishing is a cyber attacker’s method of casting “bait” to “catch” valuable information. The valuable information can then be used to reel in the prize. Phishers can make emails look very authentic, duplicating images and landing pages.
How can you spot an email phisher?
Be suspicious:
- about every email from an unknown sender
- about any email that comes from a known sender with an odd request
- about any email that contains a sense of urgency
- about any email that requests users to enter credentials (user name and password)
What do I do if I receive a suspicious email?
- FORWARD ALL SUSPICIOUS EMAILS TO HELPDESK@SAUMAG.EDU
- When an email asks for some type of action, a good practice to avoid phishing attempts is to open a web browser and type in the known web address rather than clicking on a link in an email.
- Do not open attachments or click links on suspicious emails.
- ITS can evaluate an email, the sending IP address, and help determine the authenticity.
Use Unique Passwords
It is best to not use the same password or a combination of the same password for all apps. If one phishing attempt is successful, the attacker has “keys to your kingdom.”
How can you identify a phishing phone call?
Be suspicious:
- about any phone call you receive asking for coworker information
- about any phone call for which the caller sounds like a coworker but asks for unusual activity
- about any phone call alerting you to fraudulent activity on an account but the caller cannot provide YOU with detailed account information
- about any phone call threating legal action if you do not comply with demands
- about any phone call that is identified as spam.
Did you know:
- Networks have been compromised because a phisher was savvy enough to deceive a company employee who simply answered a call, trusted the caller, and supplied critical information.
- The power of AI will cause a rise in fraudulent phone calls imitating voices of real coworkers.
- Phishers are capable of spoofing real phone numbers, making phishing phone calls seem valid.
- Phishers can sound so convincing during a phone call that by preying on fear, they can convince users an account has been compromised, (such as an Amazon account or a credit card account), causing users to provide the necessary personal information to the phisher that a genuine hack can be accomplished.
If you receive a suspicious phone call, hang up. If necessary, call the company, coworker, etc., and inquire about the subject matter for which the suspicious phone call was referencing.
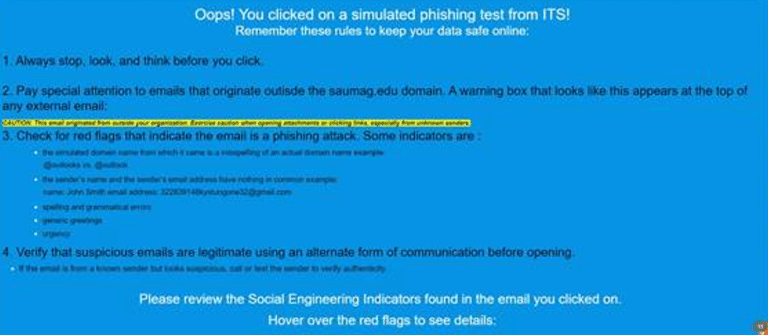
Cybersecurity Awareness Training Policy: Phishing
Annually, cybersecurity training resources are provided to SAU employees in the Faculty/Staff Virtual Center. Completion of training videos and educational material is an essential tool each member of the SAU community can use to avoid unnecessary risk to the network.
The SAU ITS cybersecurity specialist leads our phishing training efforts by participating in the industry standard practice of routinely conducting phishing email campaigns as a method of evaluating network risk.
What happens if a user enters credentials when requested in a simulated phishing campaign?
- Users who enter data, such as an SAU username or password, into a form when prompted in a phishing campaign receive educational feedback and are required to complete a 30-minute training session within two weeks of the assigned training session.
- If a user enters data a second time (which could occur during a single campaign), two additional training modules will be assigned and must be completed within a 24-hour window once notified or the user account will be disabled at the end of the workday during which the 24-hour window expires. The user may contact the cybersecurity specialist to request additional time. Contact information is provided in the assignment email. If the cybersecurity specialist is not contacted to request additional time, the user is blocked from the network until completion, and the employee’s vice president is notified as requested.
- If a user enters data a third time, the vice president and supervisor meet with the employee to discuss the importance of cybersecurity awareness.
- Should an employee enter data four or more times during a phishing training campaign, the employee’s vice president determines personnel actions, if any. ITS does not have any jurisdiction regarding personnel matters.
The purpose of phishing campaigns is to enhance SAU’s cybersecurity posture and reduce risk.